HSM Support: Ensuring Secure and Reliable Cryptographic Operations
HSM Support: Ensuring Secure and Reliable Cryptographic Operations
Blog Article
Introduction to HSM Support
A Hardware Security Module (HSM) is a dedicated device designed to securely manage, store, and process cryptographic keys. HSMs provide high-assurance encryption, digital signing, and authentication, ensuring strong data protection for enterprises, financial institutions, and government organizations.
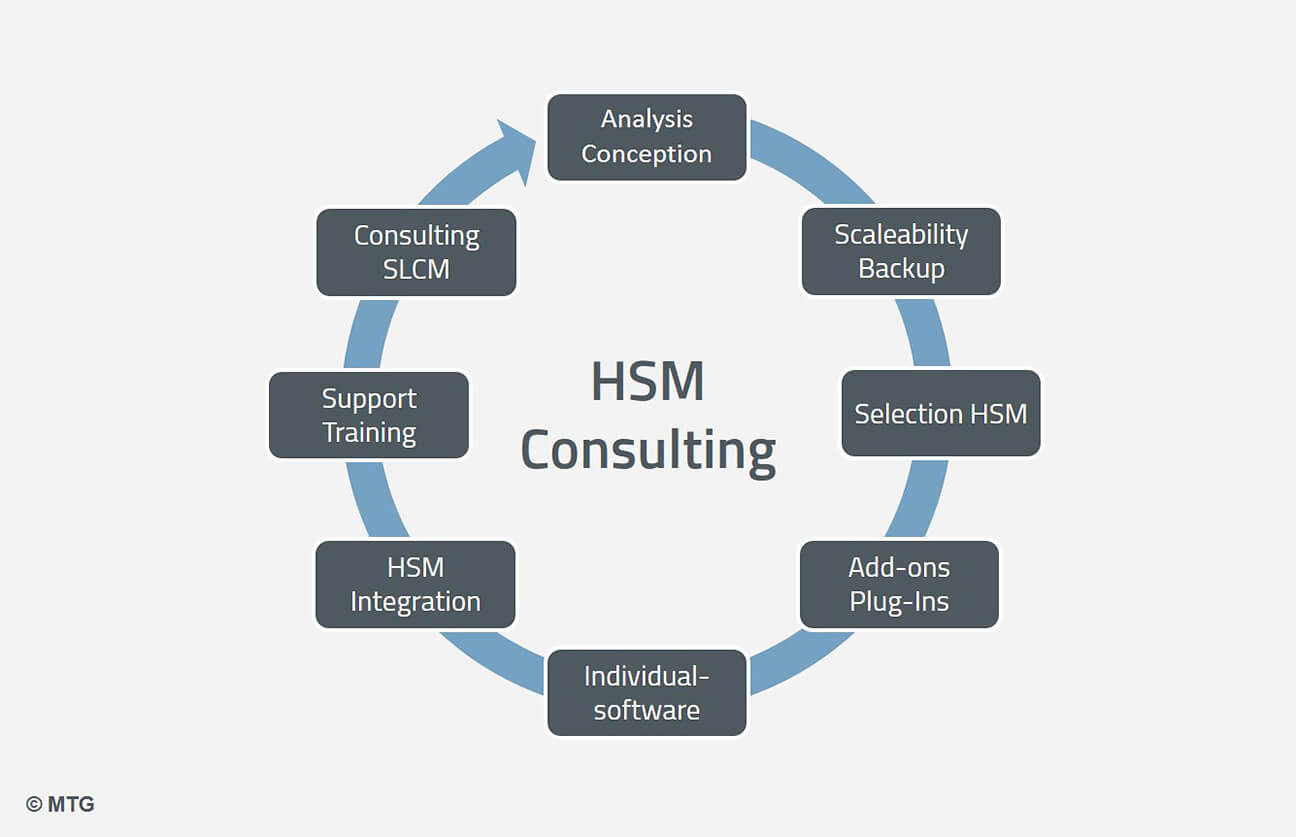
To maintain optimal security, performance, and compliance, organizations require HSM support services that cover installation, configuration, maintenance, troubleshooting, and upgrades.
Key Aspects of HSM Support
1. Installation and Deployment Assistance
Proper HSM deployment is crucial for security and performance. Support services help with:
- On-premises and cloud-based HSM setup (e.g., Thales Luna, Entrust nShield, AWS CloudHSM, Azure Key Vault).
- Network and infrastructure integration with PKI, databases, applications, and cloud services.
- High Availability (HA) and Disaster Recovery (DR) setup to ensure redundancy and failover.
- Security policy configuration to enforce access control and cryptographic operations.
2. Configuration and Key Management
HSMs require proper configuration to meet security and operational needs. Support services include:
- Key generation, storage, and lifecycle management (creation, rotation, archival, and deletion).
- Role-based access control (RBAC) implementation to restrict unauthorized access.
- Integration with PKI, SSL/TLS, and code signing applications for secure cryptographic operations.
- Firmware and software updates to ensure security and feature compatibility.
3. Troubleshooting and Incident Response
HSM failures or misconfigurations can disrupt business operations. Support teams assist with:
- Real-time troubleshooting for hardware, software, and connectivity issues.
- Log analysis and auditing to identify and resolve security incidents.
- Fault tolerance and redundancy checks to prevent unexpected downtime.
- 24/7 emergency support for critical security issues.
4. Compliance and Security Best Practices
HSMs must comply with industry security standards and regulations. Support services help organizations:
- Align with regulatory standards (FIPS 140-3, Common Criteria, PCI DSS, GDPR, HIPAA).
- Conduct security audits to validate cryptographic implementations.
- Implement dual control and quorum authentication for key management security.
- Perform risk assessments and vulnerability management to mitigate threats.
5. Performance Optimization and Upgrades
As business needs evolve, HSM performance and capacity must be optimized. Support includes:
- Load balancing and clustering to enhance cryptographic processing speed.
- Upgrading HSM models to newer, more secure hardware versions.
- Cloud migration support for hybrid or fully cloud-based HSM solutions.
- Monitoring and analytics to improve performance and security insights.
Benefits of Professional HSM Support
✔ Enhanced Security – Ensures secure key management and cryptographic operations.
✔ Minimized Downtime – Quick troubleshooting and recovery services reduce business impact.
✔ Regulatory Compliance – Helps meet FIPS, PCI DSS, GDPR, and other security requirements.
✔ Optimized Performance – Load balancing and updates improve efficiency.
✔ 24/7 Technical Assistance – Round-the-clock support for mission-critical applications.
Conclusion
HSMs are the backbone of enterprise cryptographic security, but ongoing support and maintenance are essential for ensuring availability, compliance, and security best practices. Investing in HSM support services enables businesses to manage encryption securely, prevent downtime, and stay ahead of emerging cyber threats. Report this page